DNS Hijacking And DNS Cache poisoning
What is DNS
DNS stands for Domain Name System. DNS lets users connect to websites using domain names instead of IP addresses.
The Domain Name System (DNS) is the phonebook of the Internet. As humans check the phonebook to get the phone number by name, computer query the DNS server to resolve the IP of requested domain name.
Example of Domain name : WWW.GOOGLE.COM
Example of IP V4 : 216.239.38.120
Example of IP V6 : 2001:db8:3333:4444:CCCC:DDDD:EEEE:FFFF
How DNS Works:
If you need to open any website, you need to provide the IP address to the computer. It is tough for humans to remember IP. So Humans enter the domain Name in the browser. Whereas Computer understands only IP.
So DNS server comes into the picture. DNS translates domain names to IP addresses so browsers can load Internet resources.
Any device which is connected to a network, has a IP address and that address is necessary to find the appropriate Internet device i.e. IP is like your home address is used to find a your home in city.
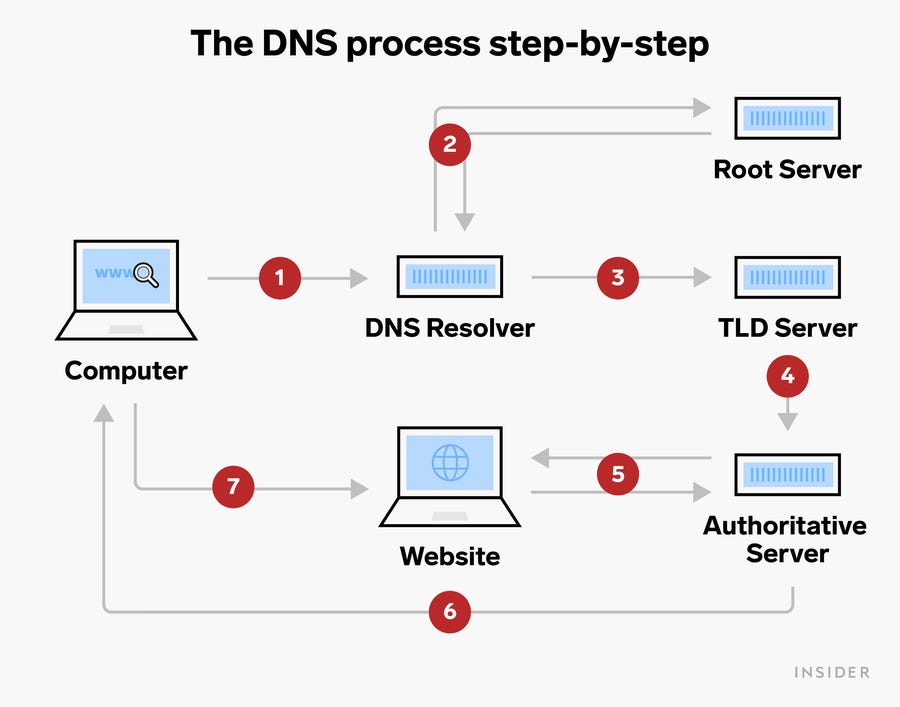
There are 4 DNS servers involved in loading a webpage:
1. DNS recursor
2. Root nameserver
3. TLD nameserver
4. Authoritative nameserver
DNS Hijacking / Redirection attack:
Cyber criminals can hack the DNS either by changing the DNS server address or intercepting the communication between your device and DNS server. After hacking, they replace the actual server IP with their site. So when you will type google.com, DNS will resolve and provide the hackers website IP, and you will be redirected to the hackers website which may looks similar to the www.google.com.
Hackers may use redirection attack for various reasons i.e. to display the advertisement, to install the malware, to display a phishing website to steal the credentials/confidential information.
Hackers generates the revenue by advertising or stealing your money directly by infiltrating the bank login details or credit card.
Real life scenario: Suppose it’s your 1st day in the collage and someone replaces classroom numbers, So you will be spoofed and you will be in wrong room. it will be more worse if mismatched room numbers get recorded in a campus directory then everyone will get lost in the campus.

Type of DNS Hijacking:
1. Local DNS Hijacking :
Hackers could use a Trojan horse virus to replace the DNS server address in the users computer. Hackers changes the DNS server settings so that the user can be redirected to the malicious site.
2. Router DNS Hijacking:
Cyber criminals could take advantage of the vulnerability in the routers firmware and change the DNS server settings. Hijacking the DNS at the router level will affect all the users connected through the impacted router.
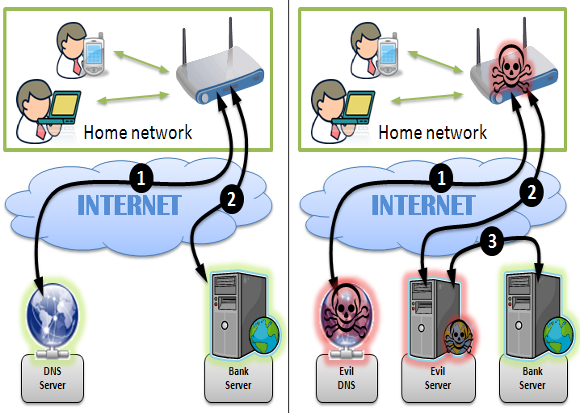
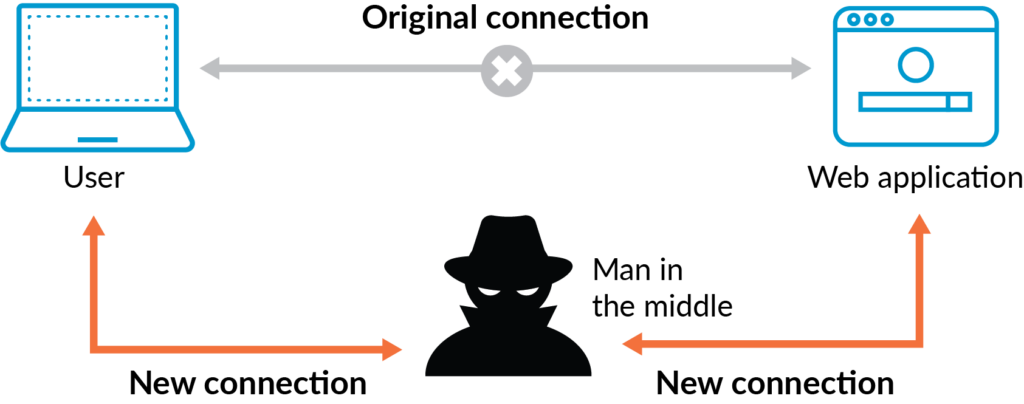
3. Man in the Middle DNS Hijacking
In Man in the Middle DNS Hijacking, hackers intercept the communication between your device and DNS server. Hackers catches the DNS server reply and replace the website server IP address and send it back to the your device.
You may not suspect anything because your organization provided laptop is not having the admin rights to change DNS settings and privilege escalation can not happen because your organization patches the endpoints frequently, moreover your OS logs are connected to the SIEM solution where privilege escalation will get detected in real time. STILL YOU ARE HACKED by Man in the Middle DNS Hijacking attack.
4. DNS Hijacking / Rogue DNS Server
Hackers identify the servers with week security and hack them. They replace the IP address of the website so whenever you try to open a website, you are redirected to the malicious site.
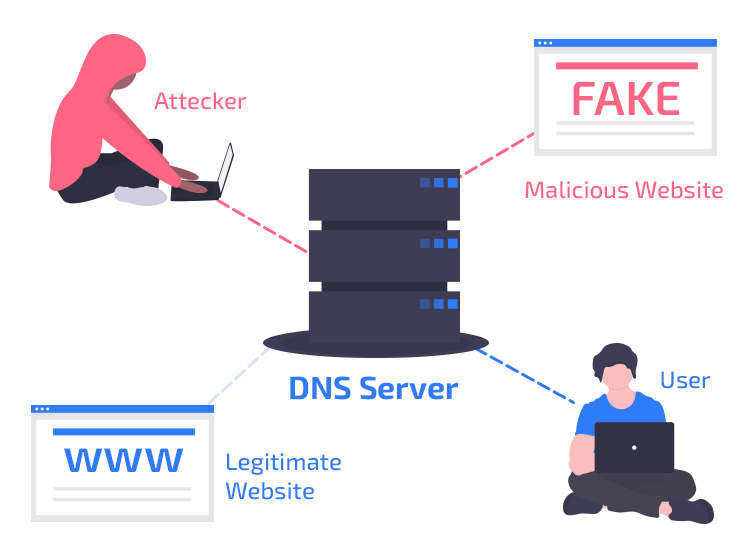
DNS poisoning / DNS Cache poisoning / DNS Spoofing
Attackers can poison a DNS cache by tricking DNS resolvers into caching false information, with the result that the resolver sends the wrong IP address to clients, and users attempting to navigate to a website will be directed to the wrong place.
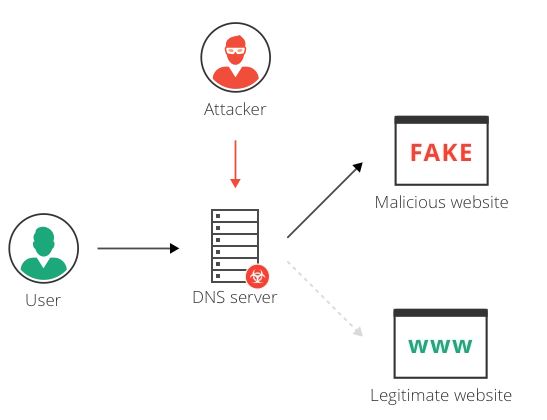
DNS spoofing is an attack in which traffic is redirected from a legitimate website such as www.google.com, to a malicious website such as google.attacker.com. DNS spoofing can be achieved by DNS redirection. For example, attackers can compromise a DNS server, and in this way “spoof” legitimate websites and redirect users to malicious ones.
Cache poisoning is another way to achieve DNS spoofing, without relying on DNS hijacking (physically taking over the DNS settings).. Attackers can “poison” the DNS cache by inserting a forged DNS entry, containing an alternative IP destination for the same domain name. The DNS server resolves the domain to the spoofed website, until the cache is refreshed. Attacker can position DNS servers cache, routers cache and computers cache DNS records.

DNS cache poisoning is a attack in which attackers spoof the DNS result without changing the DNS IP setting in your local computer. A typical DNS Cache poisoning is the act of entering false information into a DNS cache, so that DNS queries return an incorrect response and users are directed to the wrong websites.
DNS cache is used to fasten the DNS resolver process. When you open any website, its IP address is resolved by the DNS server and it stores it in the DNS Cache so you don’t have to contact the DNS server again. When next time you try to open the same website, the DNS cache stored on your computer/DNS server quickly resolves the IP address by speeding up the whole process.
Hackers poison this cache by replacing the IP address so you will be redirected to the malicious site instead of actual site.
DNS Hijacking / Redirection attack VS DNS Cache poisoning / DNS Spoofing
DNS Hijacking or DNS redirection typically involves the malware infection that changes the DNS settings on the user’s computer. The malware replaces the TCP-IP DNS server address with malicious DNS IP address. So all the DNS queries will be sent to the hackers DNS server instead of actual DNS server. Hacker can redirect you to the malicious server either entering the specific domain or every time you try to access the a site.
DNS Spoofing / DNS Cache poisoning is an act where hackers spoof the DNS records. They can use DNS poisoning to spoof the local DNS cache on your computer or DNS cache on router or DNS Cache on DNS server. These days browsers are also keeping the DNS record in the browser cache.
DNS poisoning VS ARP poisoning
While DNS poisoning spoofs IP addresses of legitimate sites and its effect can spread across multiple networks and servers, ARP poisoning spoofs physical addresses (MAC addresses) within the same network segment (subnet).
Prevention from DNS hijacking and DNS Poisoning
Since it involves the various levels so there is no one size fit solution for this attack. DNSSEC is a powerful solution that encrypts the communication between users and the DNS servers.
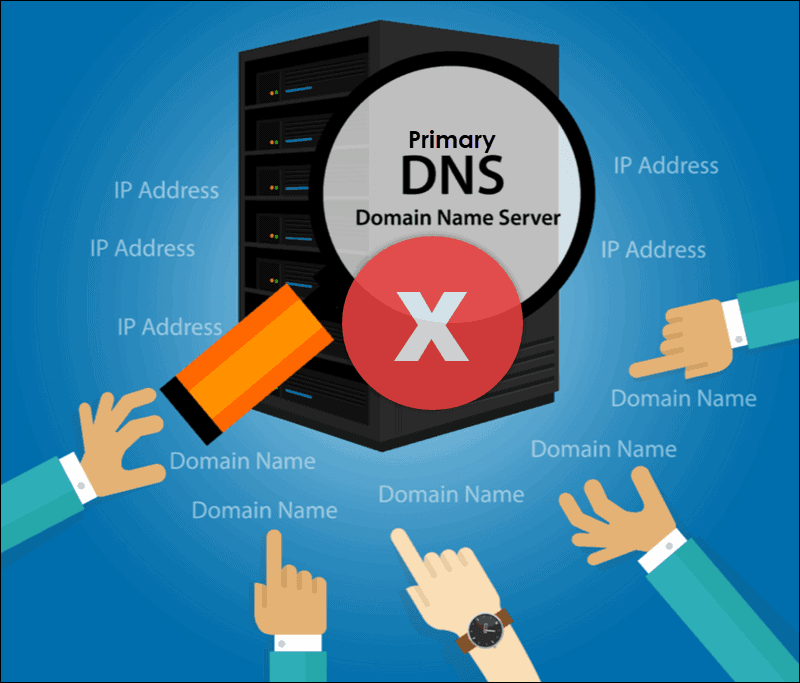
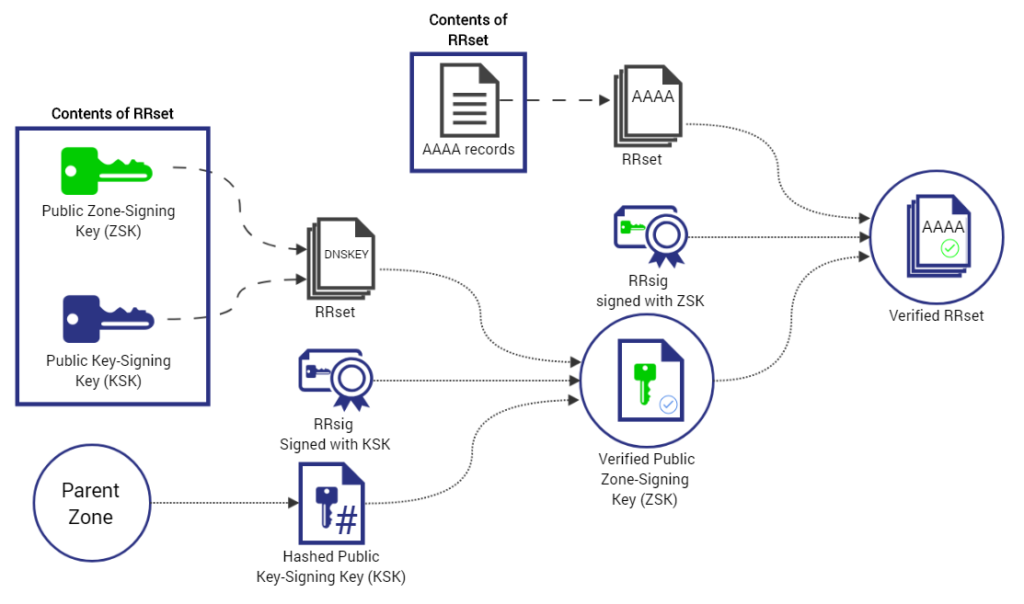
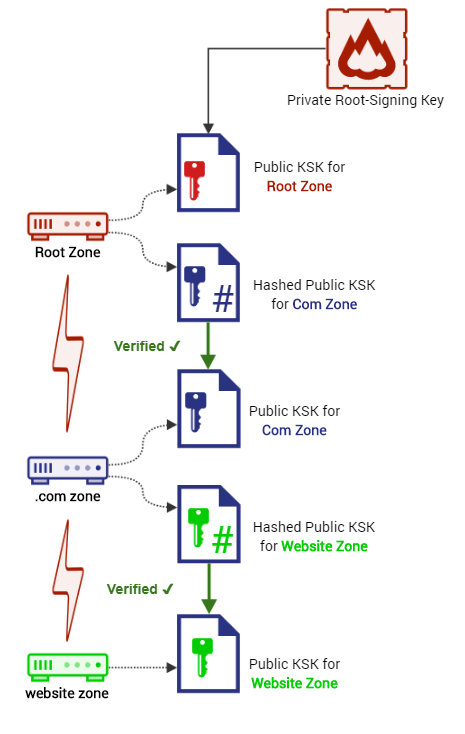
1. Validate DNS Data Integrity with DNSSEC
Domain Name System Security Extensions (DNSSEC) ensure clients receive valid responses to their queries. Data integrity is achieved by DNSSEC digitally signing DNS data provided to nameservers. When an end-user sends a query, a DNS server provides a digital signature with the response. Hence, clients know they received valid information for the request they sent.
This added layer of security helps with fighting off DNS protocol attacks. Since DNSSEC offers the data integrity and origin authority, DNS spoofing attacks and cache poisoning are successfully averted. Clients are then confident they are visiting the pages that they intended to visit.
2. Lock DNS Cache
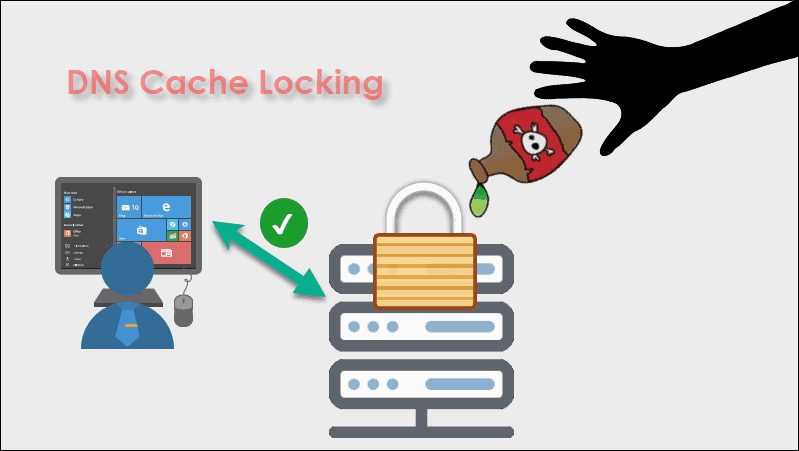
Whenever there is a query from a client, DNS finds the information and stores it in the cache for future use. This process allows the server to respond faster to the same queries. Attackers can exploit this feature by altering the stored information.
A step further from enabling DNS debug logs is locking DNS cache. This feature determines when the cached data can be changed. The server keeps lookup information during the amount of time defined by the TTL (time to live). If cache locking is disabled, then the information can be overwritten before the TTL expires. This leaves room for cache poisoning attacks.
Depending on the operating system, cache locking may be enabled by default. The cache locking scale goes up to 100 percent. When the value is set to 70, overwriting the data is not possible for 70% of the TTL. By defining cache locking to 100, changing the cached information is blocked until the TTL expires.
3. Configure Access Control Lists
Access Control Lists (ACL) are another way of protecting DNS servers against unauthorized access and spoofing attacks. Only IT administrators and system admins should have access to your primary DNS. Configuring ACLs to allow inbound connections to a nameserver from specific hosts ensures that only the intended staff can communicate with your servers.
Additionally, ACLs need to define which servers can make zone transfers. Attackers may try to determine your zone setup by sending zone transfer requests through secondary DNS servers. If you block all zone transfer requests over secondary servers, an attacker cannot obtain zone information. This configuration prevents third-parties from getting insight into how you have organized the internal network.
4. End to end encryption can be a safeguard.
5. End points should be regularly scanned via antimalware.
6. End systems should be patched frequently.

7. All the Software should be up to date with security patches.

8. Routers should not be configured with default password. Hacker can easily takeover your routers if you will not change it.

9. Install the latest firmware updates on the routers.
10. VPN: VPN allows the users to surf internet safely. There are fewer DNS hijacking chances if you are using the VPN.

11. Use secure DNS Servers i.e. Google Public DNS or internal DNS servers.


