The Internet of Things, or IoT, refers to the growing network of devices connected to the internet via sensors, software, physical things like smartphones, tablets, music players, home assistants, extreme sport cameras, virtual reality/augmented reality (VR/AR) systems, and fitness trackers and vehicles. It’s all about how data can be collected and how we can use it to make our lives better. But the question on everyone’s mind is whether or not this technology can be trusted. And if it can be trusted, what are the biggest threats?
IoT Security: Connected Device Vulnerabilities
Your smart fridge might get hacked by malware, your printer may be talking to Russian servers without you knowing, or your car might be exchanging private data about you.
A number of home and office network security breaches have resulted from IoT devices not designed with security as a core concept or even an afterthought. Once an attacker has remote access to or through an IoT device, they may be able to access other devices on the compromised network. Before installing IoT equipment, consider both the security and the security reputation of the vendor. It’s not worth compromising your security just for an exciting gadget if the device cannot meet or accept your existing security baseline.
The security issues related to IoT are often about access and encryption. To safeguard against these possibilities, here are some simple steps to take:
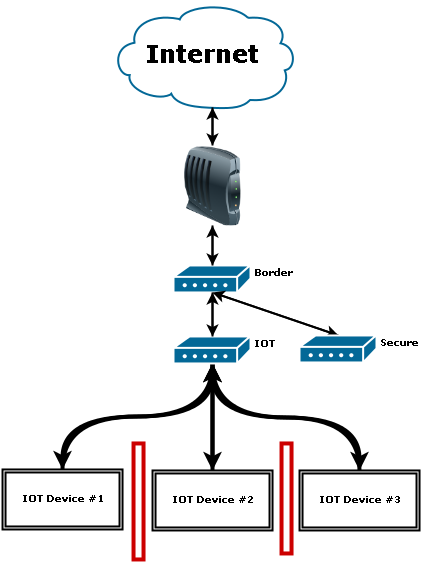
- One possible secure implementation is to deploy a distinct network for the IoT equipment, which is kept separate and isolated from the primary network. This configuration is often known as three dumb routers.
- Keeping systems patched
- Limiting physical and logical access
- Monitoring all activity
- Implementing firewalls and filtering
- Encrypt your Wi-Fi connection and keep a password (a pretty difficult password, not 123456)
- Turn off all wireless capabilities on the device if you’re not using them,
- Use an antivirus program that updates daily, update all software automatically and as soon as updates are available.
IoT Security: Sensitive Data Theft
IoT devices provide a conduit for data theft, as access is not just needed to the device, but to a connected software system. With an abundance of unsecure connections and poor oversight, IoT devices have become a target for hackers seeking to steal valuable data like customer credit card information or medical files. To mitigate this risk, encryption and network segregation can be used on both device data as well as the internet traffic that goes between your phone and the IoT system.
IoT Security: Vulnerable System Integration
While not all IoT systems are connected to the internet, the ones that are can face a whole host of vulnerabilities. IoT devices such as home thermostats, electric cars, and pacemakers are often vulnerable because they require a data connection for updates. They use email addresses, or have default passwords that are easy to find on the internet or simply guessed by hackers. Many devices can’t be updated offline, leaving them exposed without regular patches.

IoT Security: Authentication Methods
Authentication is the process in which a user or computer proves their identity so that they may access protected data.
Digital certificates, two-factor or token-based authentication, hardware root of trust (RoT), and trusted execution environment (TEE).
IoT Security: Weak Authentication Methods
The most common form of weak authentication is passwords, which are easy to steal if they are not changed regularly. This has left consumers highly susceptible to having their personal data, such as credit card information, compromised by malware. Two-factor authentication can be used to create a more secure connection. But unfortunately many IOT devices does not have MFA capability inbuild available as of now.
IoT Security: Unprotected Remote Accessibility:
The remote accessibility which IoT devices often offer is an especially high-risk feature. The ability to control a device from miles away can have harmful consequences for both the device owner and third parties. This risk is further compounded by the fact that many IoT devices do not encrypt their connections at all. As more industries incorporate these devices into everyday business practices, it is critical that increased focus be put on security when developing new software and hardware.

Cyberattacks Becoming Increasingly Sophisticated
We have always been under the threat of cyberattack, but it’s getting to the point where we are being hacked in new and creative ways. A recent study has found that 77% of all malware targets enterprise networks, which puts large-scale attacks on businesses in the spotlight. As hackers become more sophisticated in their techniques, businesses must be equally as vigilant. It is now more than ever a business owner’s responsibility to ensure that they’ve put the right safeguards in place to protect themselves from security breaches.
Healthcare Sector Targeted by Hackers
By 2025, the global IoT market is predicted to reach a value of around 2.34 trillion U.S. dollars; hackers are trying to take advantage of this increased number of devices by hacking into systems in order to steal sensitive data like personal identification numbers and credit card information which can then be used for illegal activity.
Lack of physical hardening
One big concern with Internet of Things devices is the lack of hardening the devices. If a device is not physically close to its creator and administrator, there is nothing the admin can do to ensure its safety from outside attacks. Devices that do not have a secure location and that do not permit for continual surveillance could be penetrated by a potential attacker who could gain access to invaluable information about their network’s capability which could help in remote attacks and gaining control over the device. For example, a hacker could extract the device’s memory card and view its contents, access private data and information, and do this over and over with all the devices in the network.
Insecure data storage and transfer
Unfortunately, these IoT devices are often vulnerable to security breaches, like large-scale DDoS attacks. For example, in 2016 a DDoS attack took down major websites like Twitter, Reddit, Netflix, PayPal and more. In 2018 there was another attack on the same scale. Another threat is unauthorized data retrieval or leakage from insecure personal data storage.
More people are utilizing cloud-based communications and data storage and this results in a growing connectivity between smart devices and the IoT network. Nevertheless, as more data is transferred, received, or stored through these networks, the risk of a breach or compromised data also increases. Because it does not currently contain any encryption or access controls, it is important to keep data secure during entry into the IoT ecosystem by utilizing strong security solutions like firewalls and network access controls.
Data Breaches Affect Everyone
In the past year alone, internet security has been under threat by a series of data breaches. These breaches have affected everyone from celebrities to people living in China, the US, and Russia. In July 2017 for example, Equifax revealed that 143 million people’s personal information had been exposed due to a hack on their computer system. With all this stolen data, cybercriminals could use it for identity theft purposes or to steal money from unsuspecting victims.

