Although authentication is not new, the number of authentication factors used has increased dramatically in recent years with the increased adoption of two-factor, and now even three-factor authentication. As more authentication factors are used, it’s important to understand what each factor does and how they work together. This article will explain the anatomy of authentication, going into detail about each type of factor that you can use to authenticate your users.
Authentication:
Authentication is the act of validating that users are who they claim to be. This is the first step in any security process. With the increasing frequency of online fraud, it’s vital to use an authentication process that makes it difficult for someone else to pretend to be you. This means using more than one type of authentication factor (something you know, something you have, and something you are) as well as making sure your password is hard to guess.
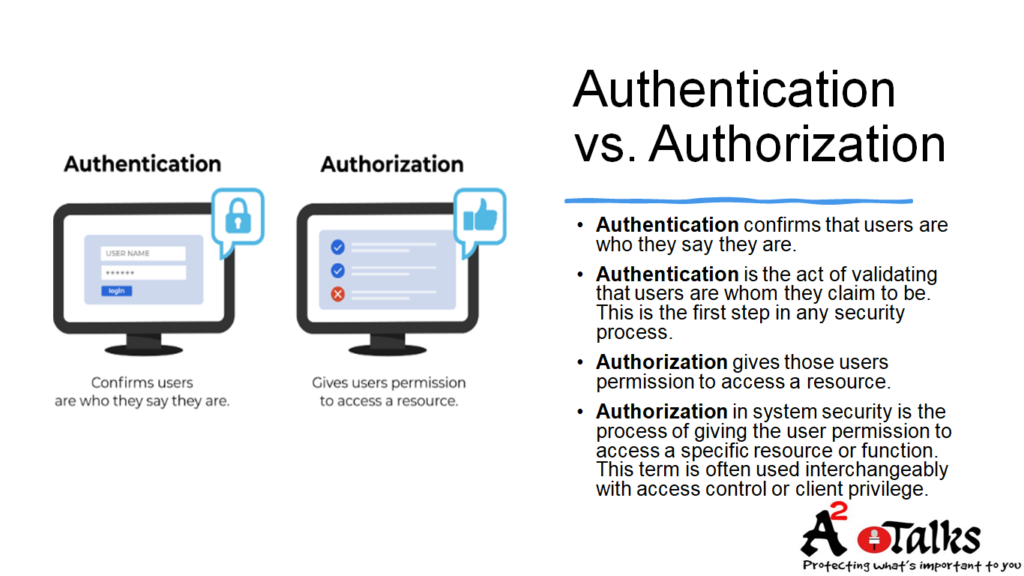
Authentication VS Authorization:
It is important to understand that authentication and authorization are not synonymous terms. While authorization is related to authentication, it does not necessarily mean one leads to another. Authorizing a user within a system (or granting them access) means determining if they should be allowed to perform certain tasks. Whereas, authentication means establishing their identity within your system by validating their credentials, and ensuring that they are who they say they are. This provides the foundation for authorized users within your application. So what’s all this mean?
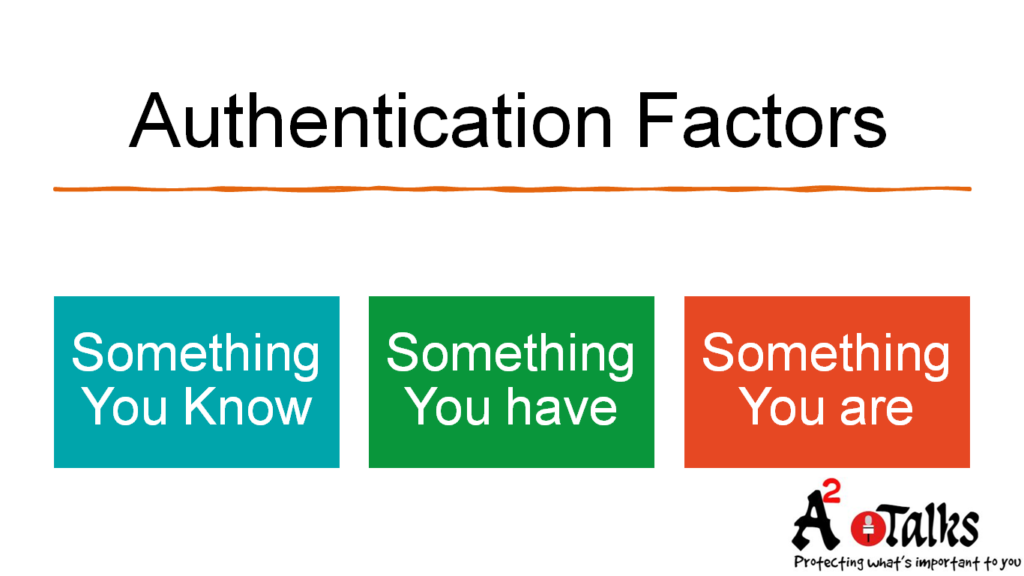
Authentication Factors:
There are three factors:
- something you know
- something you have
- something you are
Something You Know:
Something you know is any piece of information that is uniquely tied to an individual, like a password or pin number. Some examples include social security numbers, birthdates, mothers’ maiden names, and pet names.

Something You Have:
Something you have includes tokens, access cards, credit cards, ID cards, driver’s licenses, and keys to your home or car.

Something You Are:
A person’s physical traits can serve as their signature in the biometric method of identity authentication. A basic example is iris recognition, in which the eye’s unique hexagonal pattern can serve as a harder-to-duplicate key than something more basic like what you know or what you have.

Pros And Cons With Each Authentication Method:
Pros And Cons With Something You Know:

Pros And Cons With Something You Have:

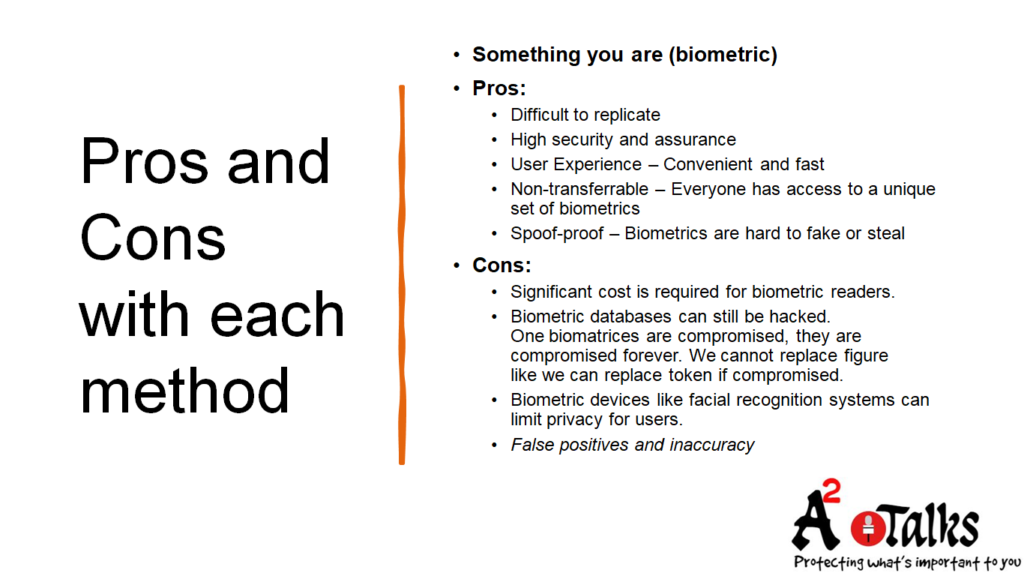
Prod And Cons With Something You Are:
Two-Factor Authentication (2FA):
Two-factor authentication requires that a user present two different pieces of evidence (or factors) to verify his or her identity. With 2FA, a user might have to enter a numeric code texted to their phone as well as their password when logging in, or they might have to insert an ATM card and then input its PIN number. In most cases, 2FA offers better security than single-factor authentication. There are three types of authentication factors: something you know, something you have and something you are.
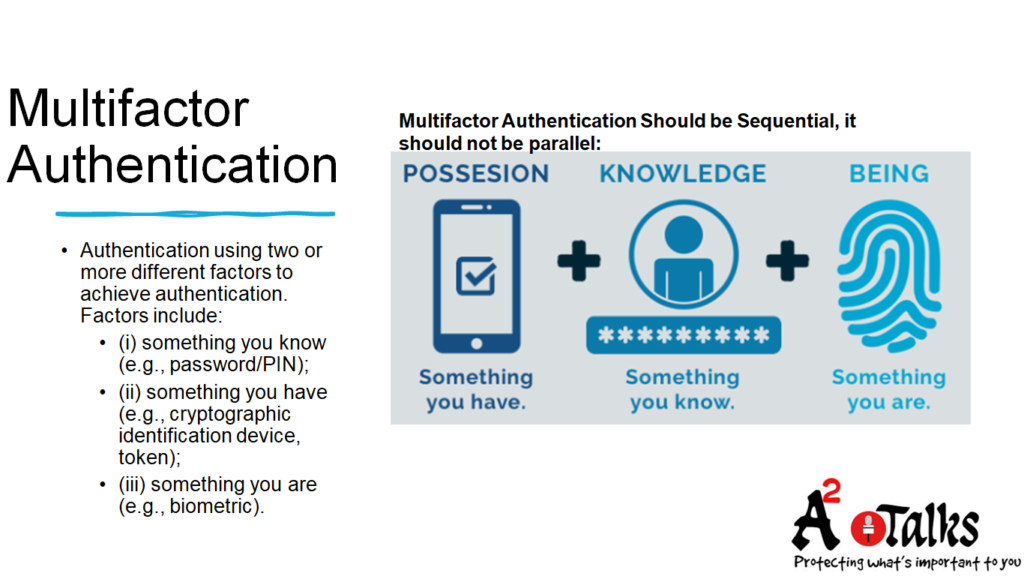
Multifactor Authentication:
Multi-factor authentication (MFA) is a process that requires two or more proofs before you can gain access to something like an app, an account, or a VPN. MFA is a core component of a strong identity and access management (IAM) policy. One might say that rather than just asking for a username and password, multifactor authentication lessens the chance of a successful cyber attack.
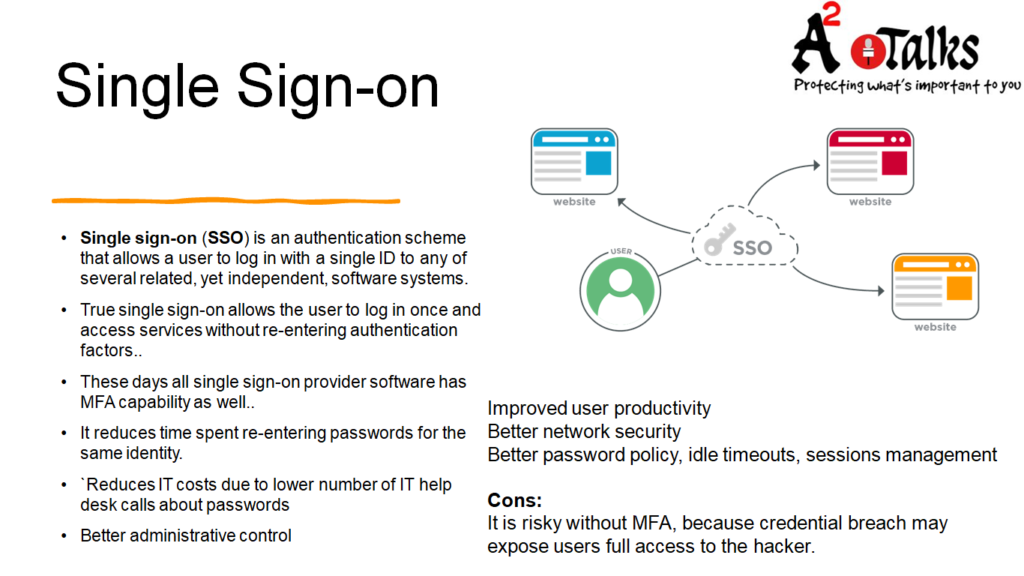
Single Signon:
Single Sign-On (SSO) is an authentication method in which a user logs into one application with a set of credentials and, by virtue of that fact, gains access to all applications and services accessible through that initial system. Most of the SSO solutions are enriched with MFA capabilities. When properly deployed it prevents unauthorized users from accessing user accounts in your organization.
True single sign-on allows the user to log in once and access services without re-entering authentication factors..
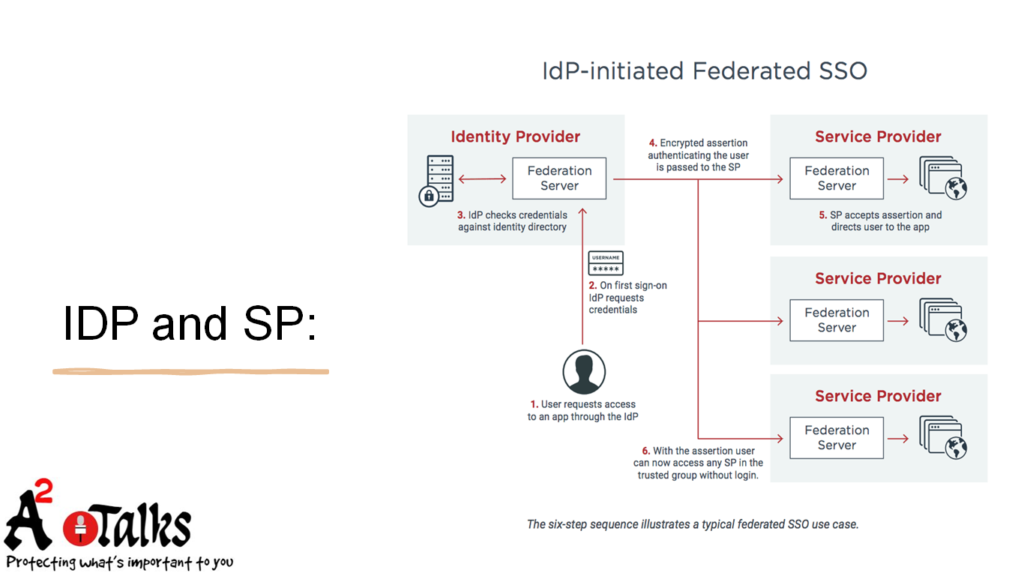
Federated Single Sign-on:
A method for enabling single sign-on functionality across multiple domains or organizations, independently operated identity providers (IdPs). This is an approach to Single Sign-On whereby a user presents a single set of credentials to gain access to multiple applications hosted in multiple domains. With federated SSO, an identity provider acting on behalf of one application authenticates a user and then securely delivers authentication information to another application. Federated SSO is typically used by enterprises that are spread across multiple geographic locations or that are part of larger organizations.

Identity Provider(IDP) – Service Provider (SP):
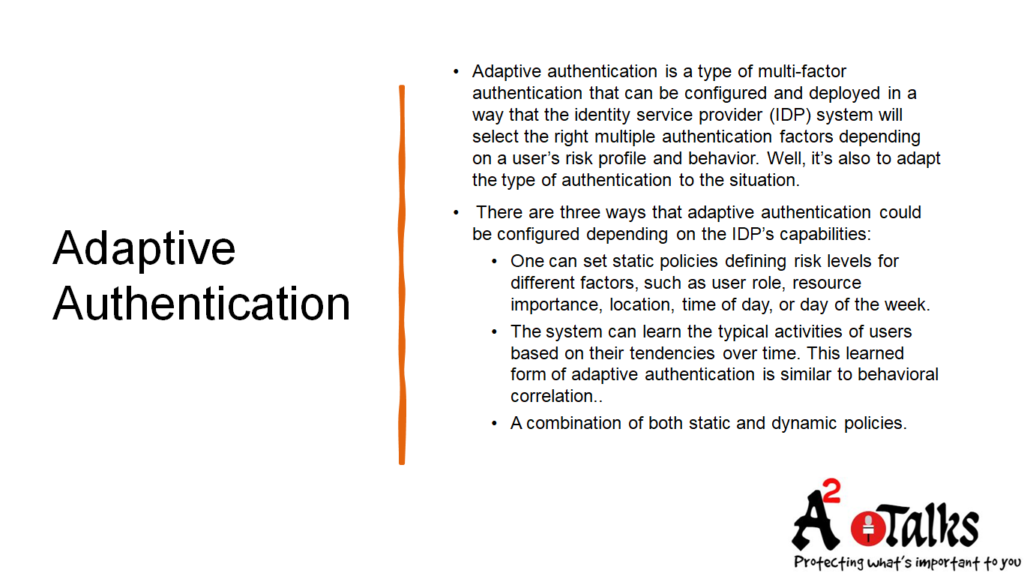
Adaptive Authentication
Adaptive authentication is also known as adaptive multi-factor authentication, adaptive authentication is based on context and activities. This method uses multiple factors in different combinations depending on a person’s situation, risk score, and location, such as where they are logging in from, their typical login times, device type, and more.
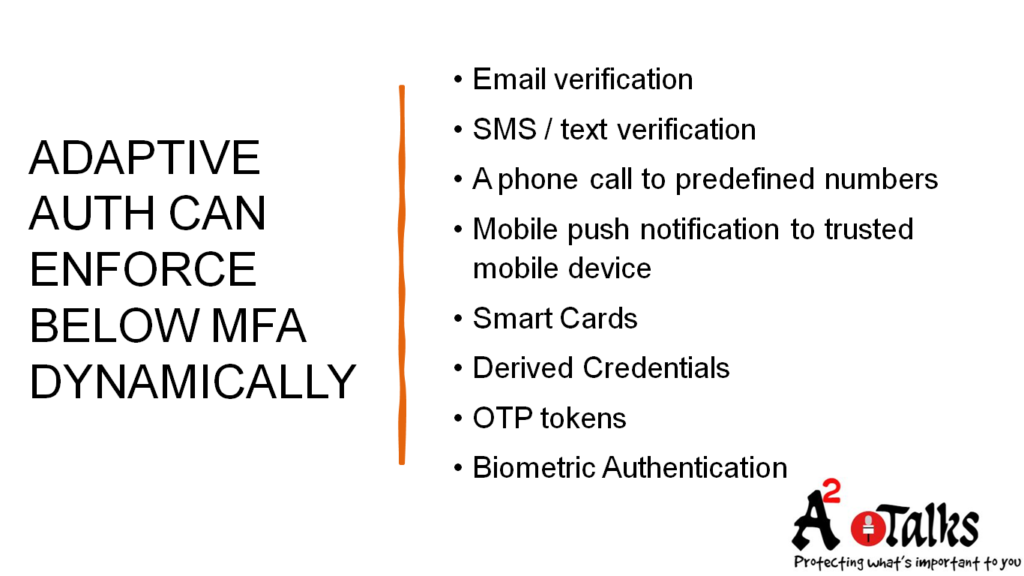
Adaptive Authentication Can Enforce Below MFA Dynamically: