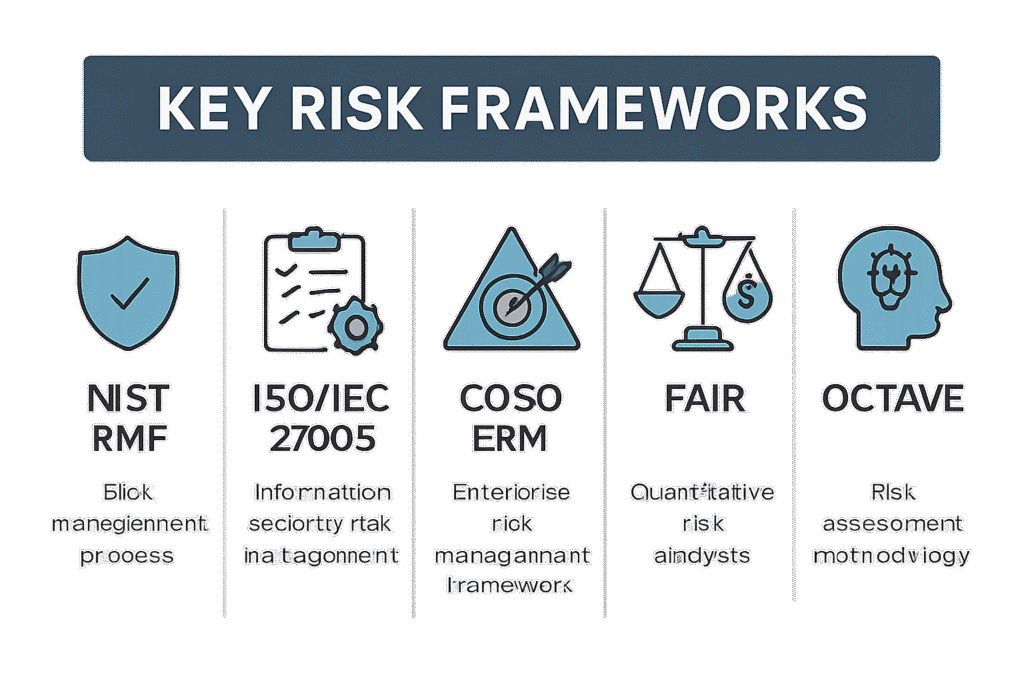
Most important security models for CISSP exam
Classic security models form the foundation of information security, helping organizations control access to sensitive data and preserve its confidentiality, integrity, and availability. These models were developed decades ago for military, government, and enterprise applications—and their principles still influence modern security. Below is a practical, easy-to-understand overview of the most important classic security models for […]
Most important security models for CISSP exam Read More »